
 Rising Antivirus Free Edition
Rising Antivirus Free EditionRising Antivirus Free Edition protects your computers against all types of viruses, Trojans, worms, rootkits, and other malicious programs. The ease of use and Smartupdate technology make it an “install and forget” product and entitles you to focus on your own jobs with your computer. The Rising Antivirus powerful engine has been certified by Virus Bulletin, Checkmark, TUV.
Rising Antivirus Free Edition has many key Features including Proactive defense technology, patented scanning technology for unknown viruses, patented fully automatic SmartUpdate, Virtual Machine unpacking engine, application protection, self protection, hidden process & rootkit detection, program startup control, malicious behavior detection, computer security check, and a file Shredder.
The interface is quite easy to use and it offers different settings for advanced users. One of the downfalls wtih Rising Antivirus Free Edition is that it sometimes comes up with false positves - meaning it will tell you that there is a virus, trojan or worm when there isn’t one. That, for the most part, is better than it not finding anything at all. Another benefit of this antivirus software is that it only uses limited resources so you can continue to surf the internet without it bogging down your computer.
Rising Antivirus Free Edition is a solution with no cost to personal users for the life of the product while still provides the same level of detection and protection capability as Rising Antivirus 2008. Version 20.63 may include unspecified updates, enhancements, or bug fixes. The free version offers the same level of protection as the commercial version but does not include a firewall or the support you get with the paid version. However, it is very comparable to other paid antivirus softwares and is considerably above the other free antivirus softwares.
Avira AntiVir Personal Free Antivirus 8.1.0.331

If you are diligent about treating your computer right, and by that I mean, not opening downloads from people you don’t know, not opening messages that are unknown and so forth, the free version of Avira’s AntiVir is probably all you need to keep your computer free of viruses. Consistently rated in the top five for effectiveness, AntiVir is also low-profile. It spawns only two background services and if there weren’t a system tray applet to access the program, you probably wouldn’t even know it was running. Basically, it is extremely light on your computer. Despite this, it offers just about every basic AV feature you’ll find in the major competition.
AntiVir’s interface is easy on the eye and easy to use for beginners. Unlike some of its competitors which make it difficult to access advanced settings, it also gives you all these with a simple switch to expert mode. Probably AntiVir’s neatest trick is auto-scanning directories as you navigate though them. You can turn it off and on when you need it, so you don’t have to leave it running all the time, but at least you know you have it available to you.
Obviously, you’re not going to get every neat feature with the free version of a pay program. Most notably missing in action is an e-mail scanner, though there is rootkit scanning. Rival free competitors provides usually provide the email scanner but not th erootkit scanning so you already have a leg up. The 20-Euro premium version of AntiVir adds the e-mail scanner as well as faster updates, anti-spyware features, and a browser add-in that helps guard against malicious Web sites and downloads. It also kills the nag screen you see when you download updates.
Although its major free competitor, AVG Anti-Virus Free, may offer one or two more features, Avira AntiVir Personal Edition Free has been consistently rated as better at detecting viruses by AV-Test.org. If you’re good about not opening strange attachments, AntiVir probably a slightly better choice.
PC Tools AntiVirus Free Edition 5
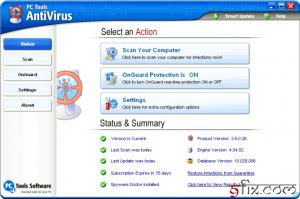
PC Tools AntiVirus Free Edition protects you against the worst cyber-threats attempting to gain access to your PC and personal details. Going online without protection against the latest fast-spreading viruses, worms and Trojans can result in infections within minutes. That’s why PC Tools AntiVirus Free Edition provides protection, with rapid database updates, IntelliGuard real-time file, Internet & e-mail protection and comprehensive system scanning to ensure your system remains safe and virus free. Version 5 features new improved scan engine, smaller memory footprint, and much improved system performance.
PC Tools Antivirus is a perfect solution if you’re looking for online protection at zero cost. It really does just as much as the higher priced programs but without the higher price. It protects you from viruses, worms, and other online threats. It has one of the nicer interfaces and the easiest to use as seen in antivirus programs and it’s really great for beginners who perhaps don’t have as much experience in using antivirus programs. It makes it perfect for users with all levels of experience.
PC Tools AntiVirus Free Edition also watches over your email so you’re protected by threats via email. It also lets you customize the scan settings so you get the protection you want and need. Unlike the pay version which is only $29.95 US, you don’t get phone support, 24/7 tech support, or high-speed updates. However, you do get access to the growing community of users who use PC Tools products. This product monitors your computer in real-time so any threat that attempts to invade your machine is going to fail. So, if you’ve been looking for a way to protect your computer from all the threats that are on the Internet, look no further than PC Tools AntiVirus Free Edition.
The Shield Deluxe

The Shield Deluxe 2008 combines reactive antivirus and spyware detection methods with the latest proactive technologies to provide your computer with the most effective protection against malicious programs. The product is simple to install and set up, while offering advanced users a range of versatile settings for fine-tuning the program.
The Shield Deluxe 2008 , powered by Kaspersky Antivirus 6.0 relies upon integrated methods to scan for viruses: the reactive method (using signature databases) and proactive protection (behavior blocker and heuristic analysis). It is optimized for use on laptops . Users of laptops benefit from an economy mode that conserves battery energy, while users of WiFi (wireless) Internet services can automatically update antivirus databases. The Shield Deluxe 2008 is installed and set up in a matter of minutes, while the context-sensitive help function helps users quickly understand the finer points of the program’s capabilities. Also, the program regularly notifies users of its current protection status and gives recommendations for dealing with virus epidemics and potential threats.
One of the best things about it, is that it monitors the activity of programs and processes that have been launched in the computer’s memory and, at the same time, warns users of any dangerous, suspicious or hidden processes and of unauthorized changes in routine processes. It works to control the status of the system registry and notifies users of any suspicious objects or attempts to create hidden keys in the registry.
The protection for email is excellent. The Shield Deluxe 2008 scans email traffic for viruses according to the protocol via which it is sent on any mail program, while plug-ins and treatment for viruses in Microsoft Outlook and Microsoft Outlook Express mail databases are offered. Lastly, All HTTP Internet traffic is scanned for viruses in real-time, ensuring that infected objects are not saved to the computer’s hard disk. All in all, it is an economical antivirus software that really does the job that you need it to do by protecting your computer from various viruses and threats.
F-Prot Review

F-Prot for Windows is an easy to install and use antivirus program that has a great interface. Although the interface would be more user-friendly if the options were available from the taskbar instead of from the Start Menu or desktop, it still has many of the features that beginner users would enjoy and find easy to use. All of the options are straightforward and practical. Some of these options include right-click, on-demand, on-access and scheduled scanning.
F-Prot claims their scan engine uses very low system resources and therefore runs under Windows 2000, XP or Vista, which means less time sitting and waiting and more time internet surfing. The RealTime Protector scans all files your system accesses for viruses. The built-in Scheduler automates tasks like updating the virus definition files and scanning which is extremely convenient. The program is simple to configure, but still gives you plenty of options. The on-demand Scanner is used to manually scan your files, folders and drives. You can also scan a file, folder, or drive from within Windows Explorer by right-clicking and selecting “Scan”.
In general F-Prot has advanced heuristics-based detection that can defend well against new and unknown threats. It has a fully automated virus signature file updates and software upgrades which make it efficient, and the email protection is in real-time which protects against attachments. And with advanced detection against malicious programs, you can’t beat the overall software. Although the Help and Support is not as good as it could be according to some users, there is an online database that contains answers to frequently asked questions for your convenience and with the low price, you can’t go wrong with this antivirus program.
Norton Internet Security 2009

Symantec’s antivirus products have historically always provided excellent detection and removal of malware. On the downside, that protection came at the price of often crippling system performance. Norton Internet Security 2009 has met that challenge head-on, finally providing a fully capable security product without the enormous overhead. Indeed, performance tweaks are the hallmark of Norton Internet Security 2009, which features ‘pulse updates’ to deliver more frequent and thus smaller signature updates, whitelisting to streamline scan times, and a lighter, sleeker footprint that installs in mere minutes.
Norton Internet Security 2009 features multiple sensors that monitor the activity levels of various components to make smarter decisions about what actions it should take - and when. For example, gamers will appreciate sensors that detect full screen mode in conjunction with gaming - suppressing non-essential alerts while still offering full protection in the background. Mobile users won’t have to worry about laptop batteries draining because they forgot to disable a scheduled scan. Norton 2009 detects when a battery-powered laptop is idle and delays the scan accordingly.
Norton Insight makes note of trustworthy applications found on the drives and adds those applications to a whitelist so they aren’t unnecessarily scanned in the future. This type of integrity checking got its start with behavior-based scanners and is well suited for streamlining the performance of signature-based scanners as well. The first time you scan it may take an hour or more while it checks out all the files, but subsequent scans should finish in well under that .
In addition to the standard signature detection, Norton Internet Security 2009 includes SONAR. Browser protection is also built-in, detecting attempts to exploit known vulnerabilities. The rules-based protection isn’t as proactive as it could be and the browser protection is a bit signature-based in practice, but both features still add considerable protective value to the product. Don’t be swayed by Norton’s past performance - this latest version is definitely worth a try.
G DATA Antivirus 2008

G DATA Antivirus 2008, formerly AntiVirusKit, is a simple and effective antivirus solution. It doesn’t include many perks, but does include the basics as well as a couple extras that have come to be expected in the antivirus software market. Overall, it is an easy-to-use product that will keep your computer protected. The main configuration and information page has most of the functions that you will need. If there is an option on that page that you can’t find, there is an Options page that includes some more advanced configuration options for each section of the program.
The best part of G DATA Antivirus 2008 is that there isn’t much user intervention needed. The default configuration is sufficient for most home users and if you set the scans to a time when you are not using your computer there is little chance you will even notice the program running at all. While slow, the antivirus engine within G DATA is very thorough. It is also nice that it doesn’t eat up many resources while scanning. Updates for G DATA Antivirus are downloaded every hour by default.
G DATA Antivirus doesn’t come with a whole slew of extra features. It does include a two part antivirus scanner that is rated very high and also includes an email scanner and a heuristic scanner. Installing G DATA Antivirus is as simple as following the prompts and letting it run. After you are finished with the installation, there is a significant update to the software that needs to be downloaded.
Support for G DATA Antivirus 2008 is a little bit small to say the least. All that is included at this point is an incomplete FAQs section and a support request form on their website. But, in the overall scheme of things, G DATA Antivirus is a simple and effective antivirus product.
Panda Antivirus 2008

The new Panda Antivirus 2008 is one of the easiest-to-use and most intuitive protection software for your computer. Just install it and forget about viruses, spyware, rootkits, hackers, online fraud and identity theft. You can chat, share photos and videos, bank and buy online, read your favorite blogs or simply surf with complete peace of mind. Along with the new Collective Intelligence technology, the solution is now much faster than previous versions. Coupled with a new truly automatic update system, Panda Antivirus 2008 takes advantage of your Internet connection to transparently update the virus signature files incrementally. It is one of the first truly “install-and-forget” antiviruses for the home user.
Panda Antivirus is adequate at what it claims to do: detect, block, and remove viruses and virus attempts from your PC. However, it is lacking in speed, resource use, and independent testing. Upon install, Panda will scan your system thoroughly and then remove any viruses or malware it finds. This is great, except the software doesn’t tell you what it removed, nor did it give us the option to choose to remove the infected files. For most people, this “set it and forget it” feature will be adequate, but some might prefer more control over what files Panda removes. After all, the software may accidentally remove a file that we needed by accident. When it comes to Panda Antivirus 2008 is great for rootkits as well that can be used to hide threats and prevent them from being detected, as its reinforced protection system can detect threats that use this stealth technique.
There are the standard features that include antispyware, antiPhising, and protection against dangerous websites, the antiRootkit and free automatic daily updates. It can block hackers and intruders, even through Wi-Fi connections. Although not as advanced as some would like, Panda Antivirus 2008 is absolutely fine in keeping your computer safe.






























