Firefox and Internet Explorer both offer to save passwords for your favorite sites, but neither offer a comprehensive way to manage those passwords, nor a method to easily change the saved data. In addition, neither browser pre-fills your registration and checkout forms.
Password Profiler 2 is a complete rewrite of our automated password filler. This new version allows you to:
• Log into Web sites automatically
• Fill long registration and checkout forms quickly and easily
• Save logins to your favorite sites
• Share logins between IE and Firefox
• Maintain multiple profiles allowing you to fill forms based on your needs, like whether you want to use personal or business information
Password Profiler 2 features:
• An advanced artificial intelligence to properly fill forms
• Encryption to protect your passwords and data (if you choose)
• Non-intrusive password saving and filling (if you choose)
• Low resource use
• Support for IE 6, IE 7, and Firefox
Installing Password Profiler 2
When you install Password Profiler 2 (PP2), it will ask if you'd like to install the Firefox and IE add-ons. If you use both browsers make sure to select both. After the initial install, a wizard will appear to walk you through information about PP2. At the end of the wizard, it will let you choose if you'd like PP2 to automatically save forms with passwords and if you'd like to automatically fill forms that have been previously saved. Whatever you decide to choose now, you can always change your preferences from the Edit | Options menu in the program.
If you install the Firefox extension, Firefox will launch and ask if you would like to install the PasswordProfilerFF.xpi. Select Install Now and the Firefox Add-ons manager will appear with a button prompting you to Restart Now. Once you push the button, Firefox will be restarted and you will see the Password Profiler program icon in the bottom right corner of the browser. Clicking (left click) on the icon will display the Password Profiler popup menu.
If you install the IE add-on, the Password Profiler icon will appear in the toolbar of IE 6 when you restart it. In IE 7, Password Profiler will appear in the chevron ">>" menu in the toolbar.
Form Filling
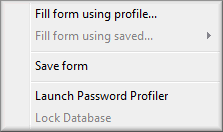
Now that the program is installed, you can configure PP2 to fill in Web site registration, banking, and checkout forms. From within IE, click on the PP2 toolbar button; in Firefox, click on the PP2 icon in the status bar. A menu will appear providing five options:
• Fill form using profile… – this is used to fill a registration, bank, or checkout form with saved profile data you create
• Fill form using saved… – this is used to fill a login form with data saved from the last time you logged in to the site and saved the data
• Save form – this saves the login information and other data that you've enter into the form on the current Web page
• Launch Password Profiler – this opens the PP2 program window
• Lock Database – this locks the PP2 database preventing unauthorized access
Select Launch Password Profiler and the main window will appear. On the left side (labeled 1 in the picture below) is a tree showing a folder that contains a default profile called "Internet." This profile contains several items related to the profile. These items are:
• User – this item contains information about you or the alternate user you want to create. Fields include first and last name, date of birth, birth place, and gender
• Address – this item lets you enter the address, city, state, ZIP, and country for the profile
• Contact – this item contains all your phone numbers, e-mail address, and associated Web sites
• Credit Card – this item lets you enter card information like type, number, CVS, name on card, and expiration date
• Banking – this item enables you to enter information about your checking accounts
• Login – this item lets you enter the username and password that you commonly use when you register at a new site
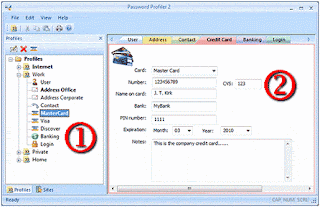
You can create additional data items in each profile. For example, if you occasionally register at sites with your work address, you can create a new address item by clicking on the current Address item and selecting the New Address button that appears at the top of the profile tree. You could also right click on the profile or any of the data items and select Insert Address. You can then enter the information about the item (see 2 in the picture above). Each data item can be renamed for easy identification. For example, you might have a Home address and a Work address. You can also select which data item should be set as default by right clicking on the name and selecting the Set as default menu option. Default items are displayed in bold text and are listed first when filling a form.
Now that you've filled in profile data, you can quickly and easily register at sites, enter banking info, or check out quickly from online stores.
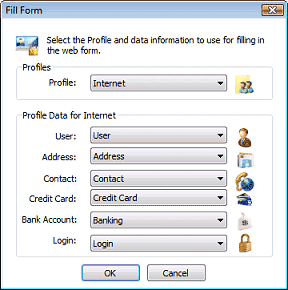
When you're done filling in your profile information, close PP2's main window and go to a site that you'd like to register at. Once there, click IE's PP2 toolbar or Firefox's PP2 status bar icon and select Fill form using profile… A dialog will appear allowing you to select a profile to use for filling the form. Select the profile and click OK. If you'd like to use a different set of data from the profile rather than the default data, for example your work address, just make sure to select the appropriate profile data before hitting OK.
Passwords
PP2 offers a lot of flexibility in how to fill and save passwords. In developing this utility, we found that everyone seems to like to have passwords handled differently. Some people like a window to pop up announcing that PP2 has a saved password for the page. Others, like me, prefer to take an action in order to save and retrieve the password.
In the Options dialog there is a tab that contains the settings for auto-saving and auto-filling. If you'd like to have PP2 automatically save forms that contain passwords, select the checkbox next to this option and then select whether you want PP2 to prompt you before saving or not. If you choose to have PP2 prompt you, a dialog box will appear whenever you submit a password to a new site.
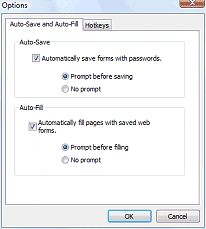
Similarly, you can choose to have PP2 automatically fill pages with saved form data. If you select this option, you can also select whether it should do so with a prompt or without.
If you don't want to have PP2 do any auto-form filling or auto-form saving, you can perform these actions in two different ways. To save a form, select the Save Form menu item from PP2's menu or use a hotkey that you've assigned. To fill a form, you simply select the menu choice Fill form using saved… which allows you to select a pre-existing saved form, or you can use a hotkey
Password Profiler's Database
PP2 uses a database to store your profiles and logins. Occasionally you may want to perform maintenance on this database. In the File menu are four database-related options:
• Restore Database… – this opens a dialog to select an existing backup to replace the current one
• Backup Database… – this item allows you to select a location to back up the current database
• Database Info… – this lists information about the database, such as how many records are in the database and the last time it was backed up.
• Compact Database… – this allows you to shrink the size of a database that has gotten large over time and has had many records deleted. It is important to not interrupt the compaction process once started or else you risk corrupting the database
Additional Features
Master Password
If you use PP2 in an office or on a laptop, or perhaps if you're concerned about security at home, you can lock down PP2 so that it requires a password to use. From the Edit menu, select Edit Master Password… This opens a dialog that allows you to create a master password. It asks for the password, a confirmation of the password, and a reminder phrase to help you remember the password.
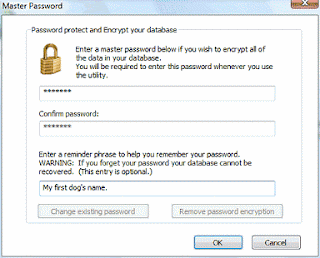
PP2 does not store your password anywhere on your system, or even in the program's memory, so it is imperative that you do not forget it. Lost passwords cannot be recovered. Because the password is not retained, you will need to enter the password whenever you launch the PP2 Editor, or a new browser session.
Reporting/Printing
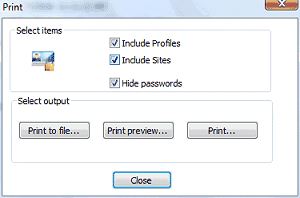
You can print out all of your profiles and saved site forms. You can also create an HTML file to view them outside of the program. Simply hit the Print button in the toolbar and select if you'd like to include profiles and/or sites and if you'd like to hide passwords. Then hit the Print or Print to file button.
Window Style
PP2 also features a method to change the look of the program. From the View menu, select Application Look. The default look is Office 2007 Blue Style. However, you can select an appearance from eight other styles like Window 2000, Windows XP, Office 2003, and more.
Release Notes
PP2 is a complete rewrite of the original Password Profiler (PP). As such, it was not possible to extract the dataset from the original PP and import it into PP2. If you previously used PP, you will need to recreate your logins.
In order to provide more flexibility in matching passwords with sites, URLs stored in the database are not encrypted. This may be a concern to some people who choose to use a master password to lock down PP2. Please note that this does not affect stored passwords. They are still encrypted.
Password Profiler 2 does not support Authentication Dialogs. These are Windows dialog boxes that are displayed by your browser to prompt for user credentials. Password Profiler 2 only supports Web Forms at the current time.
PP2 has not been thoroughly tested with the beta version of IE 8. PP2 will probably need to be updated to function with IE 8 when IE 8 is officially released.